Check your dark web exposure
Enter your business email to identify threats to your organization like malware-infected employees, stolen session cookies, and recency of breach exposures.
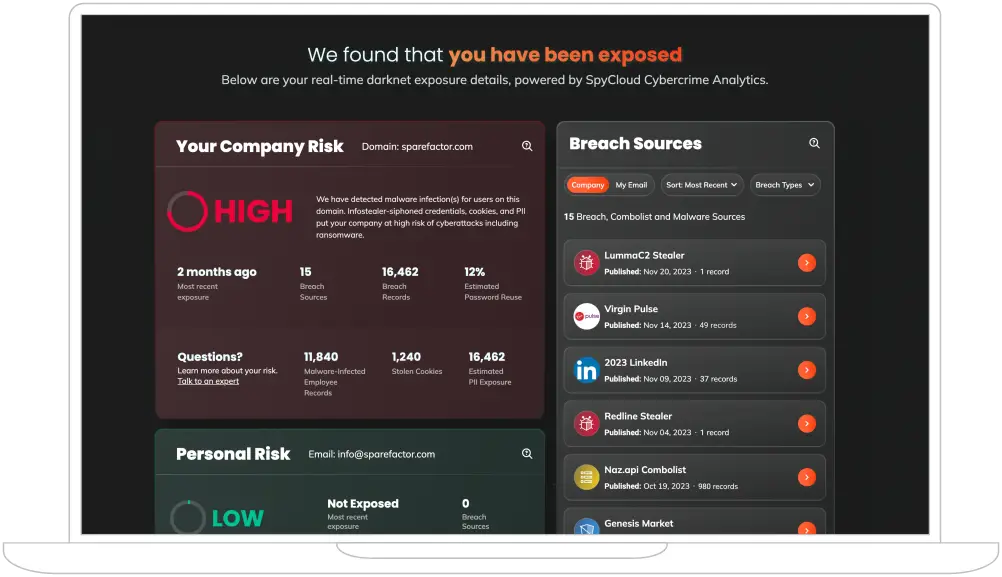
How It Works
1
Enter your email address in the box above and select the “Check Your Exposure” button.

2
SpyCloud will run a dark web check against the data we constantly recapture from the criminal underground and deliver details about your company’s risk, as well as your personal and customer risk.

3
Get the full report by email, where you’ll see your details unmasked – including malware-infected users, stolen cookies, and exposed PII.
SpyCloud Use Cases
SpyCloud delivers automated protection from ransomware, account takeover, and online fraud with solutions powered by Cybercrime Analytics.
Protect Your Enterprise from Cyberattacks
Act on exposed workforce authentication data before criminals can use it to perpetrate ATO and ransomware attacks
Streamline Consumer Account Security
Protect your bottom line by combatting synthetic identities, ATO, and fraud tied to malware
Power Cybercrime
Investigations
Draw on decades-worth of digital breadcrumbs to unmask criminals attempting to harm your organization
Partner with SpyCloud to Power Better Products
Become a SpyCloud Data Partner
Build powerful products that leverage the SpyCloud API to provide value to your consumers. Our data enhances Dark Web Monitoring Solutions, Identity Theft Protection Apps, Anti-Fraud Platforms, Payments Solutions, Cyber Insurance Underwriting Platforms, Threat Intelligence Platforms & more.Become a SpyCloud Reseller
Learn how you can expand your customer base by partnering with the leader in account takeover and fraud prevention.Act on what cybercriminals know about your business
Put an end to ATO, ransomware & online fraud with Cybercrime Analytics

